Setting up a pivoting and kerberoasting lab
Because I feel like being fancy, I have decided to go on the journey of setting up a fully functioning lab for me to attack in a similar vein to OSCP/HTB labs. This is for two reasons; first and foremost is to improve my infrastructure/sysadmin skills. For the foreseeable future this is my career track, so if I can turn study into a fun exercise I will be more likely to engage with it and continue to excel.

The second is I wish to perform things in the labs that simply wouldn’t fly in any other commercial pentesting lab environment. I want to deploy disgusting malware, perform phishing using user automation frameworks to simulate little beanbags who fall (or not!) for my scans, and perhaps most of all I want to feel secure in the knowledge some dickhead isn’t going to revert the box I am 9 hours deep in (I am looking right at you, Poison

This first exercise will be a fairly simple dual purpose lab; a two machine domain to practice pivoting and attacking a machine you have no physical connectivity to, and an environment to practice various kerberoasting attacks via SPN abuse (perhaps others as I develop this segment, but that will be another post).
To ease ourselves into the process of hax0rman again (as I have realistically not done any serious works in the pentesting space since passing my OSCP on 11/11/19), we will use server 2012 R2. This opens up a slew of attacks to us since it really is just 2008 in disguise.

This will not walk you through how to install a VM. If you need THAT sort of handholding, this might not be the type of article you are going to get value from. Refer to the about page for more information on what this blog is about. Try one of these links for help on setting up vms.
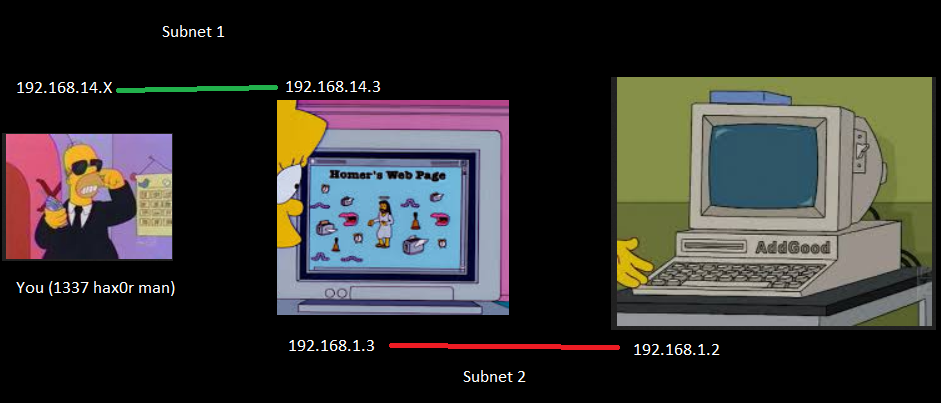
Two vms (one domain controller, one web server), one domain, two private networks. “Public” access will be through the web server (WS) who has two NICs; one touching the domain controller (DC) and one for regular access. I say “public” because we will put these on host only networks with no real internet access. Feel free to be a rebel and expose these to the real world, I won’t stop you; I will genuinely laugh if something bad happens though.

Set up your VM adapters so we have two different private networks; the addresses are arbitrary and I have already forgotten what strange rationale I had for the specific scopes I chose.
Install DC, and set it to one of those subnets. This machine will have only one NIC. If you didn’t set a good password for your administrator account when building the VM, do that now. Rename the machine, install AD Services, promote to domain controller, add a new forest and name it. Run these in an elevated PS window.
Rename-Computer -NewName DC
Install-windowsfeature AD-domain-services
Import-Module ADDSDeployment
Install-ADDSForest -CreateDnsDelegation:$false ` -DatabasePath "C:\Windows\NTDS" ` -DomainMode "Win2012R2" ` -DomainName "dirty_sprite.net" ` -DomainNetbiosName "dirty_sprite" ` -ForestMode "Win2012R2" ` -InstallDns:$true ` -LogPath "C:\Windows\NTDS" ` -NoRebootOnCompletion:$false ` -SysvolPath "C:\Windows\SYSVOL" ` -Force:$true
Install-WindowsFeature RSAT-ADDS
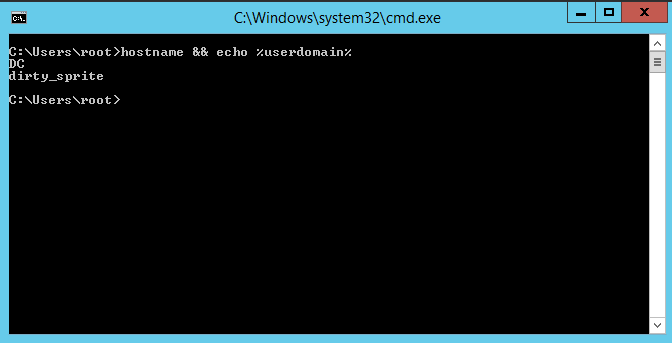
I have chosen this name because I was halfcut on monster ultra (also known as /sips/) mixed with whisky because I wanted to try replicate this strange, extremely potent thing I had in Japan from one of the literally thousands of Lawsons that are fucking everywhere in Tokyo. It had the texture and flavour of soft drink but with 9% alcohol per can, made by Suntory and called ZERO or something. It came close and I got ripped real fast, so mission accomplished I guess.

Now we are going to create a user. This little guy will be the one to serve us apache. dsa.msc will bring up ADUC. I called my user testicles with the password testicles, set the password to never expire and prevent user from changing it. Here is a PS command to do the same thing for the domain; the /domain switch says to not make him a local account on DC.
net user testicles testicles /ADD /DOMAIN
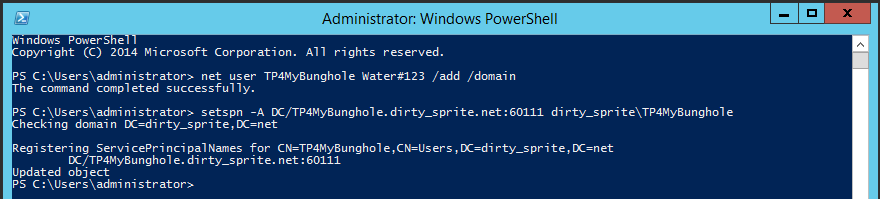
In order to perform the kerberoast attack, we need to create a service account with an SPN to abuse. Use the PS command above and create a new account, it can be anything. Since we are professionals we will call it TP4MyBunghole, because I am very excited to hear a 202X season of Beavis and Butthead is coming. Give it a password found in your wordlist of choice, since cracking the hash is one exercise we can do once its all built. Nothing like variety.
net user TP4MyBunghole pw_found_in_your_wordlist /ADD /DOMAIN
Set up the SPN like so:
setspn -A DC_NAME/ACCOUNT_NAME.DOMAIN.SUFFIX:60111 Domain\Account
Essentially, when a domain account is configured to run a service in the environment, such as MS SQL, a Service Principal Name (SPN) is used in the domain to associate the service with a login account. When a user wishes to use the specific resource they receive a Kerberos ticket signed with NTLM hash of the account that is running the service.
Basically mapping a service running on a server to an account it’s running as so that it can do / accept Kerberos authentication.
This is a bit of an oversimplification of the details of the process for sure, but the end result is that any valid domain user can request an SPN for a registered service and the Kerberos ticket received can be taken offline and cracked. There are a few different ways we can do this; on the box after getting a shell or using impacket remotely (since dear old testicles has such a poor password).
Weave finished with the DC. Taking a snapshot of the DC at this point is not a good idea just FYI; the webserver isnt in AD and I can’t attest to what will happen if you restore the WS who thinks it is in AD to this DC state which obviously does not have the machine we haven’t created yet in its AD. I may try and report back.

Create a new VM for WS (you are free to name these as you wish, I am not your robot supervisor), give this two NICs, set one to the same subnet as the DC and the other one to your “public” network. Rename the new machine, join it to the domain.
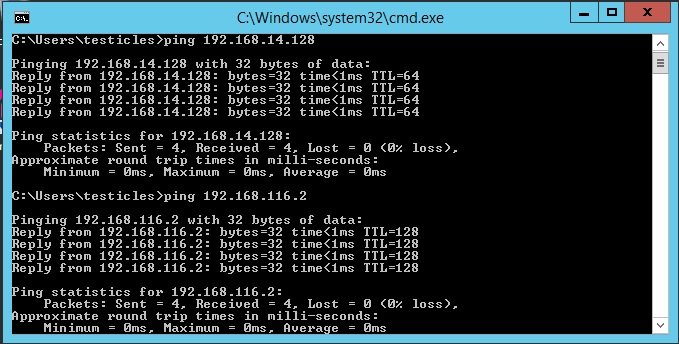
Make sure your subnets are networking instead of NOT working; from this machine make sure you can ping your attack machine (which is ONLY on subnet1) and the domain controller (which is ONLY on subnet2).
Next we want to download WAMP, because this is much, much easier than doing it separately. Before you install it, install these runtimes (assuming you have a raw R2 installation and not a patched/slipstreamed version)
https://www.microsoft.com/en-au/download/details.aspx?id=40784
https://www.microsoft.com/en-au/download/details.aspx?id=30679
We are good to install.
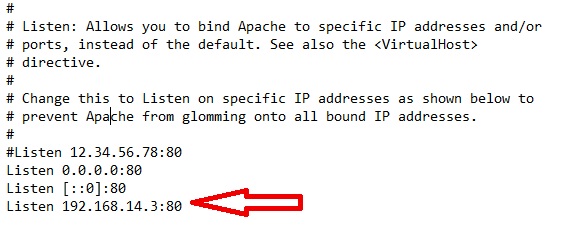
When it is installed, edit httpd.conf (wamp\bin\apache\apacheX.X.X\conf) to put the IP of the webserver and what port you want it to hang off into the “Listen” section as shown below.
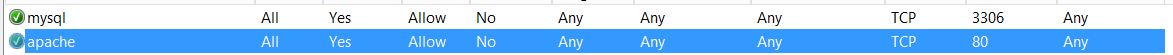
Add rules in the firewall for 80 and 3306; only the inbound is needed. If you forget this part, it will not work. It’s easy as tho.
Edit the http-vhost conf (\wamp\bin\apache\apacheX.X.X\conf\extra) to add this
Require all granted
in between the directory tags. Delete everything else in between the directory tags, as per this guide From memory this was to fix it so I can view the apache server from my attack box, where as until I did this I could only see it from local host. The issues I encountered are very very different from when I did WAMP attacks on my local box for OSCP prep that’s for sure..

Next we do some things to the database. Obviously this is a super retarded idea in the real world, but for our lab to demonstrate a technique and provide a vector we will allow remote access from ANY host to user root. Who has no password. Open cmd in the folder your mysql exe is (wamp\bin\mysql\mysqlX.X.X\bin) and feed it this:
mysql.exe -u root
create user 'root'@'%' identified by '';
grant all privileges on *.* to 'root'@'%'
with grant option;
It reads easy enough; create user root at any location, identified by nothing, give access to everything on everything to root from any location with the grant option.
But wait! Why are we creating root when we logged into sql to run these commands as root? Well turns out that localhost root and a remote location root are actually two separate accounts! The root you used to create the remote root are in fact two separate accounts. So when remote root pwns the network, it won’t be your account who did it. Technically.

Next we will make an amendment to the mysql configuration file to allow us to use the insert into outfile command. Edit C:\wamp64\bin\mysql\mysql5.7.31\my.conf and edit the secure_file_priv to ="" like so
secure_file_priv=""
Download setacl from https://helgeklein.com/download/
What this program will do is give our dear old testicles the ability to start and stop the apache and sql services. On windows these services can only be started and stopped by an admin (in pure honesty I am unsure if it is the same on linux, I just know when you catch apache shells they are www-data usually, rather than an admin).
Run the following to allow testicles to start the services
setacl.exe -on "wampapache64" -ot srv -ace "n:testicles;p:start_stop,read" -actn ace
setacl.exe -on "wampmysqld64" -ot srv -ace "n:testicles;p:start_stop,read" -actn ace
setacl.exe -on "wampmariadb64" -ot srv -ace "n:testicles;p:start_stop,read" -actn ace
Give testicles full control over the base wamp folder, otherwise you get “ah00015 unable to open logs” when you try start the services after giving control of them to your new user. I right clicked the folder and in the security tab of properties did it that way. Trying to find a PS method was taking too long when it’s about three clicks to achieve this. If you find a self-contained one liner, do let me know.

Pull up services.msc, right click, properties on mysql/apache etc. There is a tab “Log On”. Select “This account”, browse, change the scope to the domain, and select testicles or whoever you created who has no admin access. Why do we bother? Well you CAN leave it as “Local System Account” if you like, it’s just when you catch your webshell, and it will come back as NT SYSTEM. And that’s just no fun.

Restart the services, and you will see the status change to Running. If you get errors that are not covered here, check your windows event viewer, or reread these steps to see if you skipped something because I have covered much painful ground work with these strange and esoteric steps. If neither of these help, youre on your own buddy.

So now we have a basic lab setup. What can we do now we have made these strange esoteric changes?
- Remote access to SQL
- Apache server served with a domain account that is not admin, providing an opportunity to priv esc rather than a remote r00t
- Service account set up with a kerberoastable SPN
- Separate attack surface on a separate subnet accessible via pivoting
There is plenty here to play with; it’s a nice little playground for various forms of experimentation. There are many methods of escalating and moving around the domain, with and without metasploit. This post will not cover those however; this is strictly for how to build the lab. Some various ways to attack the lab will be detailed here
Congratulations you have built some infrastructure.

