Simulating discovery of CVE-2003-0344
This is going to be a very long, very large post where I pontificate quite a bit to empty out my head. There’s a lot of disparate thoughts rattling around there at the moment, and putting them into some sort of order will help.
If you wish to skip over the ranting and meandering, this will take you directly to the portion where I explain the scripts, their build process and how this may have been uncovered. Skip over the interesting parts of the blog
As I vaguely alluded to in the VST shellcode post (I don’t recommend reading it, it was a maniacal rant produced at the wrong hours of a morning to keep home grown wolves away; there is no nutritional value to be found) I have been working on multiple points of research simultaneously. This is actually the first time I have ever done this, I usually take the approach of pursuing a single goal until i kill it, then moving on to the next item. So it is strange to have two separate, disparate projects wrap up in the same weekend. It feels a little like this:

I think, I am not sure yet as I haven’t written the entire post yet, but I think this entire post can be summed up the same as it was in the post about how 2004 was the best year for gaming:

A post I saw by chompie has been rattling around my head for a while. It’s nothing but pure common sense, everyone knows what she said is objectively correct and cannot ever be disputed.
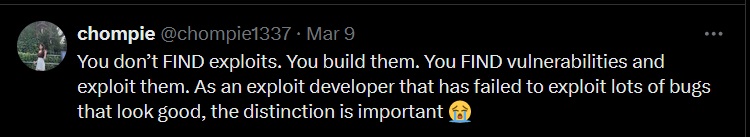
You must accept a scrot of the tweet because I have no clue how to embed tweets into markdown and I’m not going to learn. But it’s been lodged in my brain since I first saw it last quarter. It’s such a small shift in mindset that cannot be explained any better than this graphic.

How is this any easier? Well I set down this path to actually find that out. Without using the “arrived at this thought independently” madman image macro again (because it has dawned on me I have already used one from the 2004 blog as it is and am starting to beat thet same drum again) I had a thought at the start of last year about digging into old school vulns to kind of tie into the 200X schtick, as a quasi gag/callback but without any hint of irony. It has taken a while to come off the to do list because until this quarter, it never actually made it onto the whiteboard.
It is probably time to add a modicum of context to why I keep bringing this up because I am aware enough to know what I am saying is just a lot of this:

I admit that paragraph did nothing to answer the question. Another article I took a LOT of notice of this year was robots dream of root shells. And one particular phrase stood right out to me, and in a way turned the lightbulbs on in my head:
“Perhaps the inadvertent success of CGC was in highlighting how much more effective fuzzing is than other automated bug discovery methodologies, because there’s been a huge amount of energy and attention around fuzzing in the past 8 years, and not so much on all the other stuff.”
My takeaway from this is simple; despite it getting more and more traction in my feeds, fuzzing is not new. And as it turns out, it isn’t.
Look I’m not a dev. I’m a cranky ex sysad who fulfils every stereotype by being fat and drinking too much. So this “novel concept” that is older than I am, is not really something I have been exposed to before.
Improvements in fuzzing algos and methodologies are happening at a rapid pace, with things being uncovered CONSTANTLY.
This is the reason why it’s always in my feed; because people are constantly making better lap times, not because they are claiming to have invented the wheel.

So what have we established so far? Exploit development is not the finding of exploits, it is the finding of bugs, and fuzzing seems to be the most effective automated bug discovery solution. Method? Approach? I am sticking with solution, it is a term that work, as the security community and DARPA have found fuzzing to reliably work.
In a discovery that has shocked me slightly, this tweet I have been thinking about all year was only posted a month and a half ago. This is precisely why this blog needs to be written, so I can lay all these thoughts out in a straight line so I can put them all to rest. It also lines perfectly with a post from 4chan I had internalised during 2020 when I was slightly adrift with where to get started. Presented in sequence:
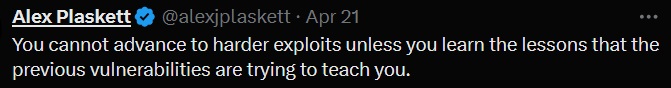
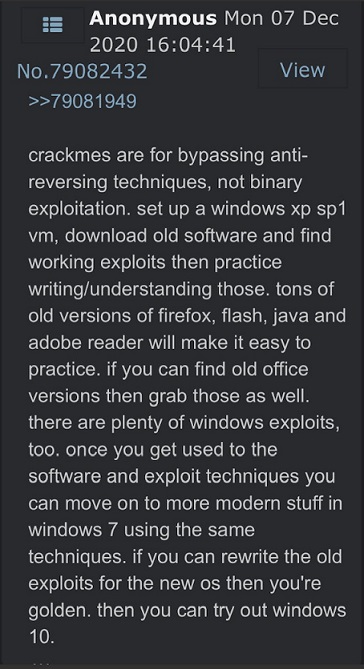
Laying them out side by side I understand now why I assumed Alex’s was much older than it really is; the sentiment has been ricocheting around my brain for years now, and much like chompies words, is “just” common sense (how I loath the word just); start with the basic stuff and progress up.
The original OSCP/OSCE progression had the right idea, stack buffer overflows in OSCP to SEH and beyond in OSCE. Progression, marked by a series of jumps. One says this is entry level, the next says this is a bit harder. I will step off my offsec bashing horse for a second to say this is not a bash, I haven’t done OSED so I don’t have an opinion on it, but it was just a fitting analogy.
Noting the caveats in the /g/entoomen post about xp sp1 being a good start, and not wanting to rediscover a web vuln (there is no one better than Louis and PentesterLab for this. I would be wasting my time trying teach myself better than he already teaches) i begin trawling exploitdb for some older vulns. And older vulns mean immunity debugger. And immunity means Dave Aitel.
This post of his on seclists went up the morning I finished this project. So it has no bearing on my pursuing this, but strongly suggests to me I am on the right path to uncover something missing from my knowledge base. While I was trying to recreate the eclipse from the first fast and the furious movie in need for speed underground 2 in 2004, people like Dave, HD Moore, Skape, Greg Linares were busting shit wide open, and doing it without stack overflow and without chatgpt.
It would be easy to insert the old man yells at cloud image again, but you are expecting it so I will not.
I bring this idea of old school chad hackers up because 1) I love to project the visage of being a hands on hips get off my lawn boomer because I instantly turn into that person the second any of my neighbours kids begin to climb my fence and 2) I am utterly fucked at development without those two resources.
“But this is important for the back half of chompies post; the exploit building half” I think to myself at first. Until I start to think about this a little more, and realise I have absolutely no clue how any of these vulns were found. Now that sort of information would do absolutely NOTHING to aid the cve, advisory or remediation advice, I just think it would have been neat, because this tweet captures very well some of the negative feelings I get towards myself when reading some writeups.
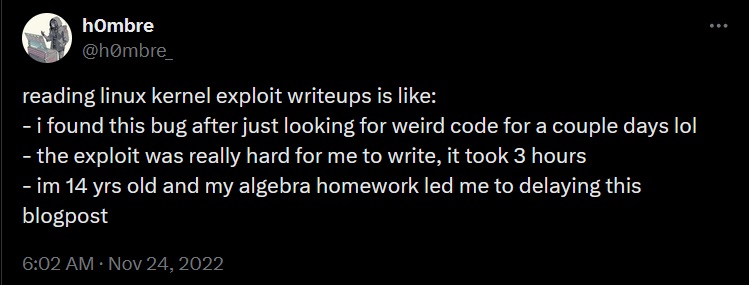
A moment of clarity did come over me last time I read this post; if we can simulate adversaries by extrapolating and reproducing the core components of an APT report without all the details, surely by that same logic we can simulate vuln discovery by reproducing the core outcomes?
So we piece all the little bits of thought together.
•Exploits are built, not found. Vulns are found.
•Fuzzing is very effective for finding vulns.
•Starting with old exploits is the way to progress.
•Dave’s lack of interest and knowledge in modern development tooling and practices say these weren’t necessary to do the work (vuln chasing) back in the day.
•A lot of vuln discovery is probably a strange mix of “secret sauce” as the metasploit crew were most likely not going to give everything away lest the cash cow flee the paddock and fucking around.
•Simulating the discovery process will probably lead us to a “close enough” representation of how it was actually found.
Because all things being fair and equal, I am willing to bet not a single person involved in chasing down CVE-2003-0344 remembers how on earth they discovered it in detail, apart from either “fuzzing” or “FAFO”. And when you think about it, what IS fuzzing but the literal embodiment of fucking around and finding out?
ENTER IE 6
MS03-020 aka cve-2003-0344 was chosen because it fit the criteria of being pre xp sp3 (by virtue of being IE6), has a metasploit module so I could unpack what it was doing by shooting it at a proxy and looking at what was being served, and was old enough that when I started thinking about this project last year, would have nicely tied into the 20th anniversary. Not that it’s notable enough to have an anniversary, but it would have been cool. Then unfortunately I got REALLY busy and it got put into that little folder called blog posts I mention in the ESXI revert panel post.

The vuln is simple enough, the object tag can cause a buffer overflow in IE when trying to render an excess of the / character. An excess in this instance actually means 65 and above. Now this is simple to exploit, but there are two different things that were discovered here; first is IE6 improperly handles the object tag, and secondly it only occurs when sent /. The other cool thing about this vuln is once it is complete, you have a complete drive by RCE. Cool as hell.
Having a bit of a think, I conclude there was most likely a singular, broader test going on; what happens if EVERY SINGLE HTML TAG one by one is forcefed hundreds of characters to induce a crash? And what if, each tag was cycled through being fed hundreds of every single ascii character?
Obviously I have an advantage knowing that this infact WILL lead to a crash, but is this REALLY any different than the type of fuzzing AFL++ is doing in this exercise to find cve-2019-13288?(forcefeeding the program until it in theory gets sick?)

So I have stumbled upon an instance where fuzzing most likely was used in the past. Fantastic, this is progress. Now given this is an xp sp1 machine, in a vm, with no ability to obtain a modern browser without effort I am unwilling to apply, no run times, no Dev environment (literally nothing of value except immunity which I am beyond AMAZED was able to run) I am faced with the prospect that I will have to script something up in vbscript and bat files.
But why not use the python environment since immunity is on the box? Should I have? Yeah, probably. But it’s taken me a long time to shake the p2 syntax from my head. I don’t even own any p2 books now, I am fully embracing the move to p3, and stepping back into using p2 will be of no positive to me.

Using the friendly robot overlord (keep in mind I said I am SIMULATING, not EMULATING so this is fair game) I ask for a large list of every single valid html tag that was in use in 2005, just to cover my bases, and to produce a sample html file that contains each tag being used in a valid manner. It can be found here.
We want to then mutate this html file, so it will start from the first tag, insert the ascii characters starting from 0 through to 126, then move onto the next tag and repeat. This is a nice little bit of vbscript, you can get it here. I am enjoying doing a little bit of vbs and wsh scripting as I reproduce some of of the things I see in reports; more on that in the future when the appropriate C.A.P.S.U.L.E.S. module drops.
How then, if I am not attaching this to a debugger, or using any sort of instrumentation, can I tell if it’s crashed? With some real caveman type shit I tell you. The script tells IE to load the currently mutated page, waits, and kills the task. If there is an error when killing the task, this means the browser already crashed under its own steam, and therefore the page we loaded caused a crash. By not being able to close the browser, we have confirmed it has crashed. Double negatives and what not.
Except the browser when faced with a crash does not actually close itself; it sits there and waits for you to ack this little slimy pop up
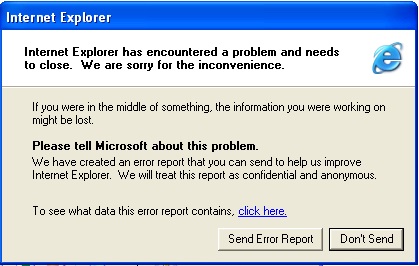
So the script is amended to call the current mutation, wait (because some of the mutations take a real long time to load), call the crash handler script which waits some more, pressed the escape key to kill the notif, then passes back to the bat script to kill the task. That handling is done by 10 simple lines, which is here. I have removed the insane amount of echo statements I inserted to try get the logic flowing, as I was actually doing the check in reverse in the bat file. I will not go into more detail.
All of this is handled by a meaty bat file, available here.
This horrific bundle of logic seems utterly stupid, and you are right, I’m sure there’s a more elegant solution, but it works and we are simulating an outcome here. The escape key has no bearing on a functional normal page, so it adds no issues!
What does add issues however, is the fact that some of these tags are used for hyperlinking. And putting targets into them (even literal nonsense ones) means IE is going to try look outside for them. And since I am not a fan of unpatched machines with operating systems older than some of my team members rawdogging the internet, IE loudly complains about the lack of internet connection, over and over.
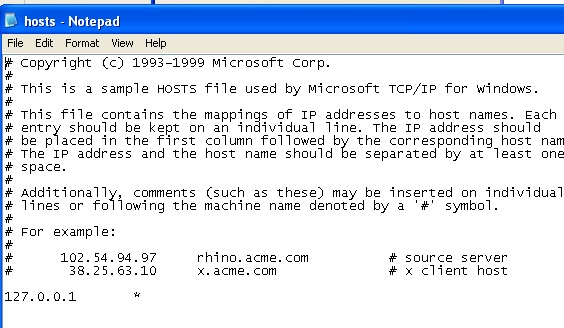
My big brain however, thought “what if I just resolve literally everything to localhost so itll shut up?” and one entry into my hosts file later and it literally worked.
After two days of mutating and looping, we receive our crashed file. Huzzah.
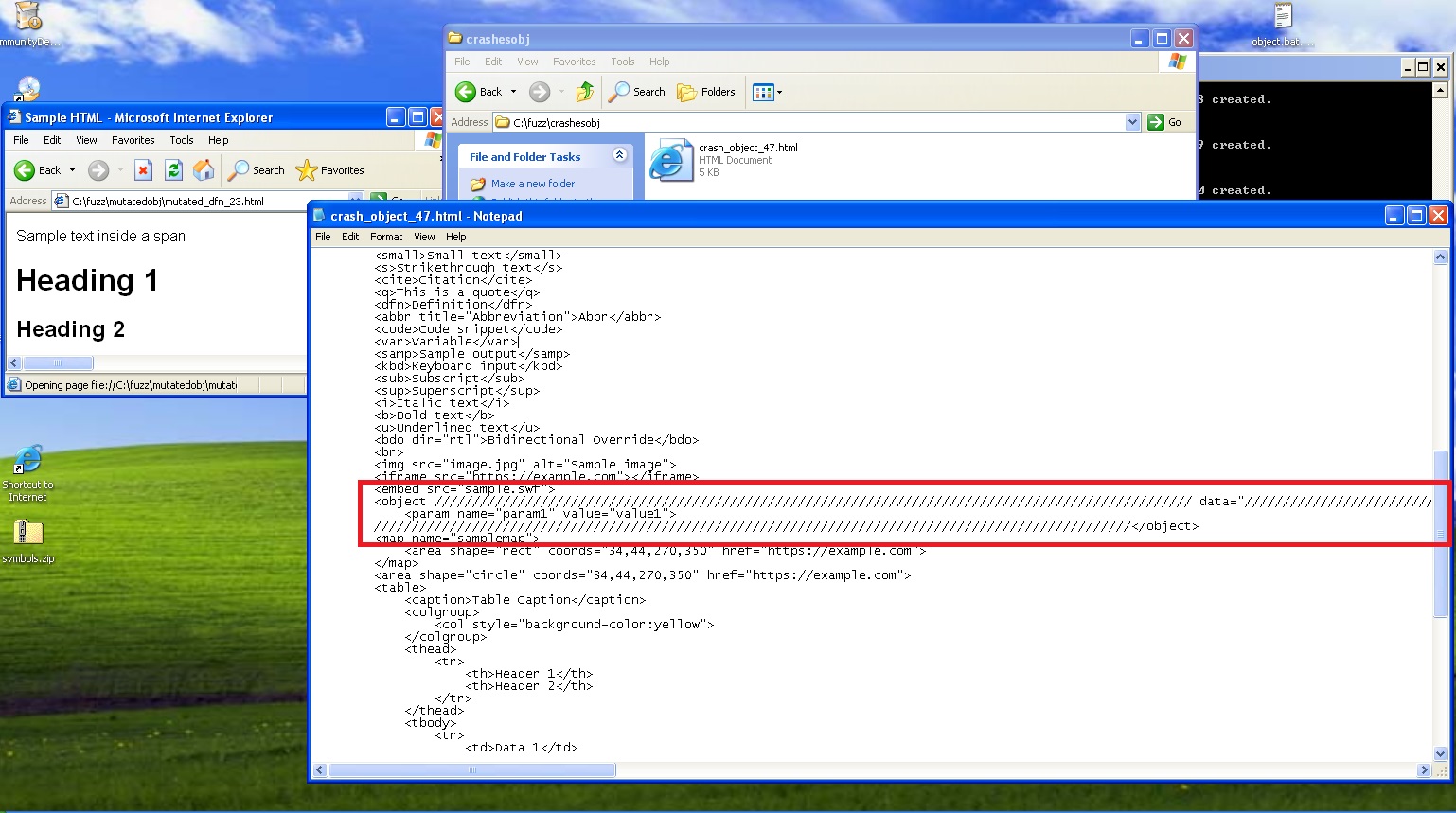
What did we learn? Well quite a lot. One, GPT has no ability to think “what if..”. Silliness is not its remit. These silly logic steps were mine and mine alone, because it just cannot think about things from any other dimension.
We have learnt that, in the absence of any information to say otherwise, researchers in the past were doing the same things we do now; try something and see if it works. It’s not silly if it gets results. Sitting a computer down for two days to try thousands of variants of different html pages was in all honesty, as much of an issue for skape then as it is for me now (basically none). Just let it do its thing and go do literally anything else.
So what is the takeaway here?
I think the big one is this, (infosec, VR, life in general) isn’t like a mathematics class; you don’t fail for getting the right answer with the wrong steps. Simulation works when you can reproduce the outcome, methodology be damned. And I don’t think “good enough” is a bad thing.
Here are three parting thoughts on this; Tim Ferris’s C+ gets you to the next grade, nakeyjakeys defence of the 7/10 game, and the F-117 being used to SIMULATE a missile.

